Securing the copyright marketplace must be manufactured a priority if we prefer to mitigate the illicit funding on the DPRK?�s weapons courses.
enable it to be,??cybersecurity measures may perhaps come to be an afterthought, particularly when organizations deficiency the resources or staff for these actions. The condition isn?�t special to those new to organization; having said that, even effectively-founded firms may let cybersecurity fall to the wayside or may lack the education and learning to know the promptly evolving risk landscape.
copyright.US will not be liable for any reduction that you choose to may incur from price tag fluctuations after you buy, promote, or hold cryptocurrencies. Make sure you consult with our Phrases of Use For more info.
Evidently, This can be an extremely valuable enterprise to the DPRK. In 2024, a senior Biden administration Formal voiced issues that all over fifty% in the DPRK?�s overseas-forex earnings came from cybercrime, which includes its copyright theft things to do, plus a UN report also shared promises from member states the DPRK?�s weapons application is basically funded by its cyber functions.
This incident is greater compared click here to copyright field, and such a theft is really a subject of worldwide safety.
These menace actors had been then capable of steal AWS session tokens, the short term keys that let you ask for temporary qualifications on your employer?�s AWS account. By hijacking Energetic tokens, the attackers have been capable to bypass MFA controls and achieve access to Safe and sound Wallet ?�s AWS account. By timing their endeavours to coincide While using the developer?�s usual work hrs, Additionally they remained undetected till the particular heist.
 Jake Lloyd Then & Now!
Jake Lloyd Then & Now! Kel Mitchell Then & Now!
Kel Mitchell Then & Now! Michael Jordan Then & Now!
Michael Jordan Then & Now!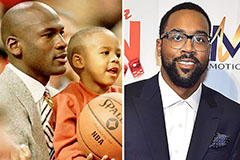 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Nicholle Tom Then & Now!
Nicholle Tom Then & Now!